The architecture will be described by the set of services within the architecture, detailing the functions these services provide and the objectives for protecting these services. The following section of the TRA will discuss how these services can be applied.
The services framework is centered around core data, application, and edge services, integrated with management and security services. See the Elements of the Services Framework diagram below. Management and security services both enable administrative access to the system. Security services assist in cybersecurity threat detection and protection, as well as the compliance with CMS security policies. The management and security services are housed in different subnets, accessible only through a virtual private network (VPN).
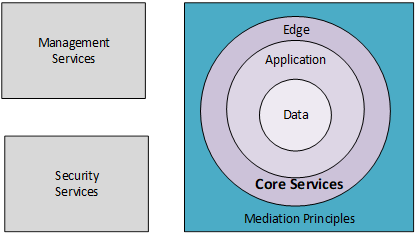
Core Services
Core services include data, application, and edge services. These services are detailed below.
Data Services
Data services are fundamental and the most basic component protecting the data. They are the components of the architecture that reside in front of and provide access to the data.
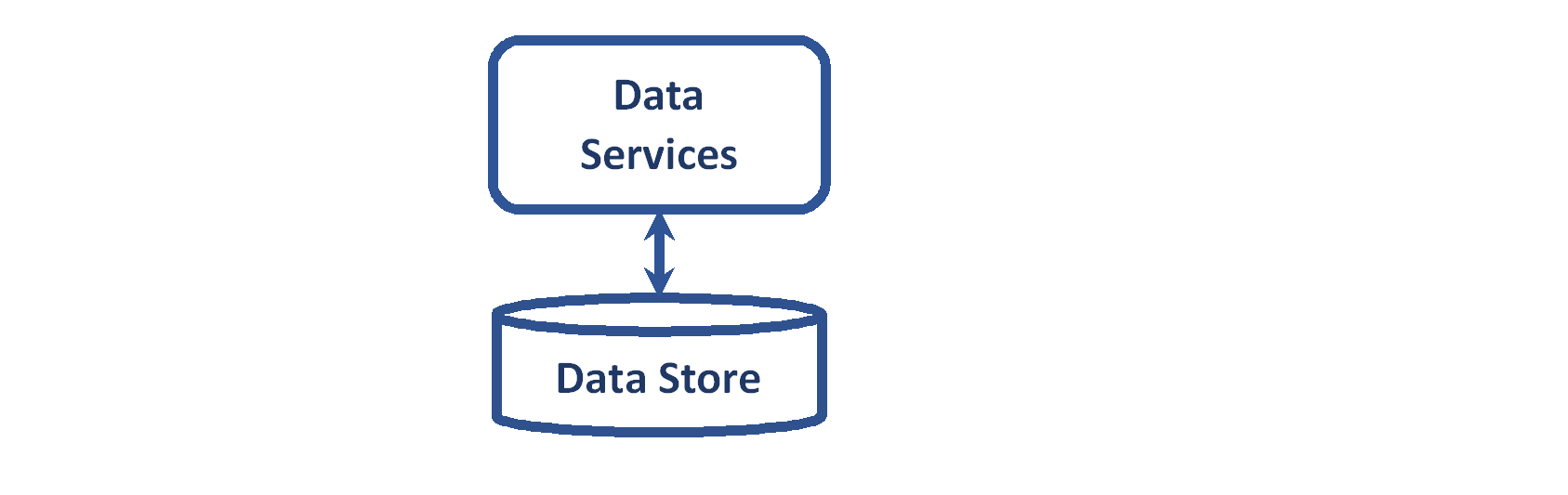
The data services must:
-
Restrict access to the data
-
Validate the caller (service consumer) has the appropriate access rights to the data services (producer)
-
Obfuscate implementation details from the consumer, not exposing data formats, credentials, etc. to the consumer.
-
CMS expects non-data services to front CMS data services. Data services are not directly accessible from outside a CMS data center.
Application Services
Application services are the components of the architecture that are generally responsible for housing the business logic. They are the consumer of data services and the producer of edge services.
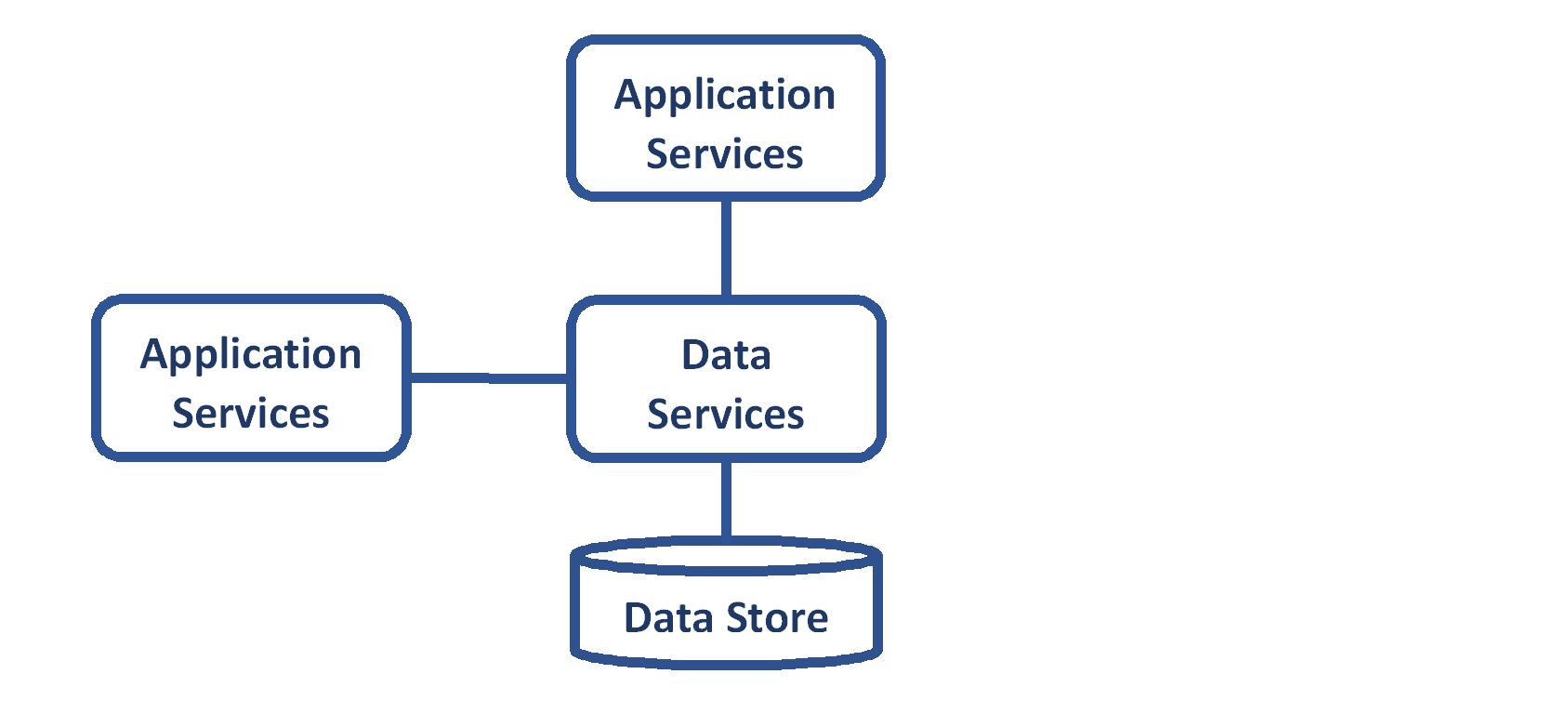
The application services must:
-
Validate the caller (service consumer) has the appropriate access rights to the application services (producer)
-
Provide access to data services
-
Act as the mid layer between data and edge services, obfuscating the access details of the data from services which are accessing that data
Edge Services
Edge services interface with external components from non-CMS systems.
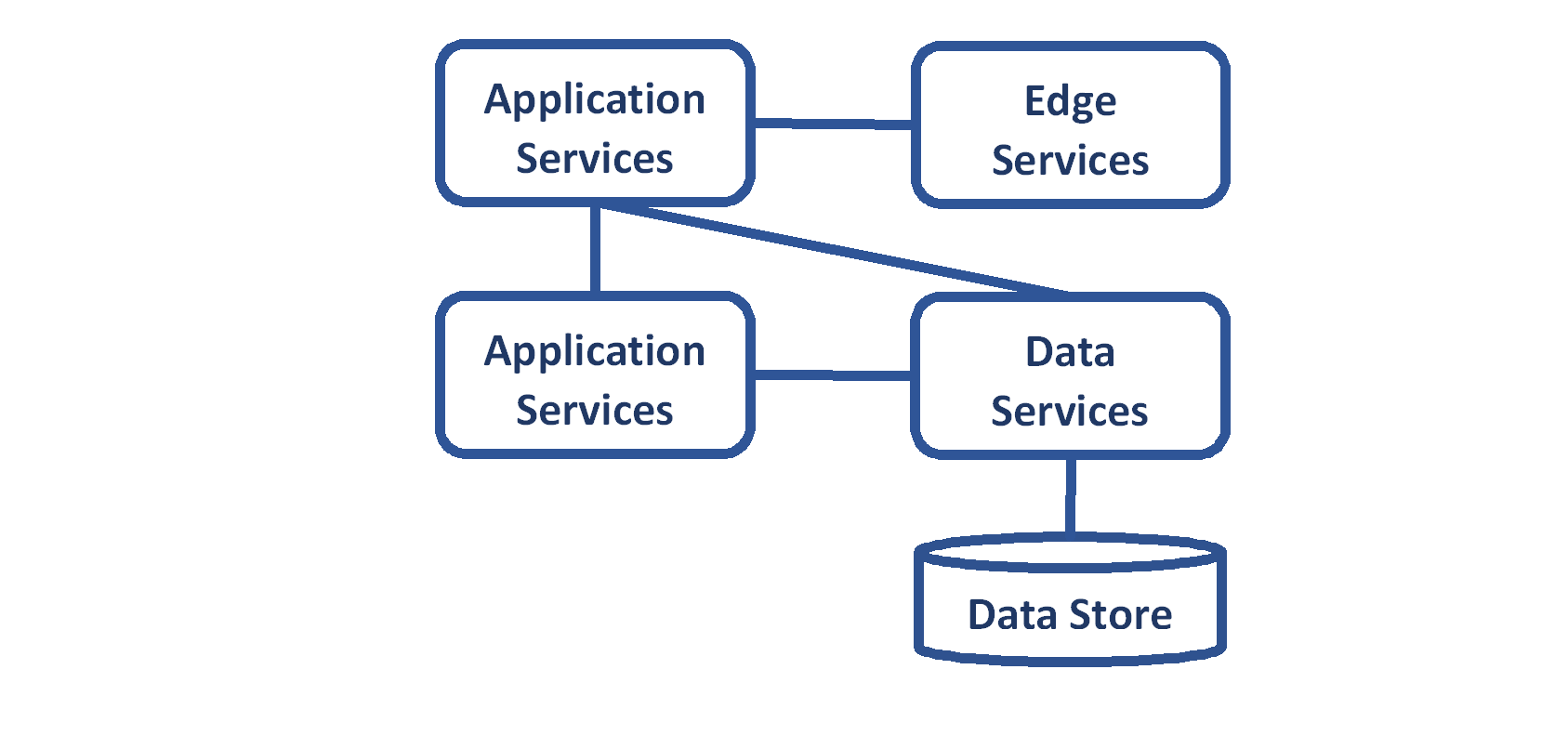
The edge services:
- Must restrict access to the application services
- May, depending on architecture, provide authentication services.
Mediation principles are implemented as part of the data, application, and edge services to enhance the security by obfuscating the access details to the data. As the request proceeds through the services framework, the request must pass legitimacy tests and be filtered or transformed to provide the necessary obfuscation of critical system components and data. An inbound data request, in most use cases, passes through edge, application and data services. Therefore, at each level, validations and transformations are performed to protect the underlying service. Some systems need to support outbound connections, and these must also follow the path out through the edge services. As outbound calls provide a ‘bad actor’ with a pathway for extracting data from a CMS data center, this pathway is restricted out to only those specific components which are required to be traversed. The outbound calls to a specific destination are also limited.
When implementing the data, application and edge services, the system designer should consider the following mediation principles:
Challenges -– Using rules to allow authorized access or the routing of messages and network packets.
Filtering -– Using criteria and rules to select data, permit a request, or check the validity of data, messages, or network packets.
Transforming -– Changing a structured request, query, result, or response, into a different structure or syntax. Changing only the headers and routing envelopes of messages or network packets does NOT qualify as transforming.
Management Services
Management services assist the system administrators in maintaining the system. The tools required are placed in a management zone, accessible only through the VPN, which provides two factor authentication.
The tools included within the management zone vary by application, but typically include the tools necessary for software releases and patching.
Security Services
The security zone houses any security tools for the application. CMS has enterprise logging and monitoring tools that are available to the system maintainers, so not all applications require a separate security zone.
CMS Services Framework - Summary
In summary, the CMS Services Framework enables applications to be orchestrated and/or composed of a service-fabric that integrates a set of services which enable access to and provide protection of CMS data. The architecture should implement a service as the authorized channel to access the application data. Users from external networks, CMSNet, or the CMS LAN must be authenticated to access the service fronting the data. Additionally, the file storage service must be configured to deny access to all unauthenticated users and all unauthorized users. Furthermore, users from external networks, CMSNet, or the CMS LAN must not have direct access to the CMS files persisted by the storage services.